Web Application Penetration Testing Guide (2026 Edition)

In 2026, the resilience of a business is inseparable from the resilience of its web applications. These applications are no longer just platforms for transactions; they are the gateways to customer trust, brand reputation, and regulatory credibility.
Yet, the threat landscape has shifted dramatically; adversaries now leverage AI-driven reconnaissance, exploit API-heavy ecosystems, and target subtle business logic flaws that bypass traditional defenses.
So, the question is no longer “Do we test?” But, “How do we validate, continuously, that our applications can withstand real-world attacks?” Web application penetration testing has become a strategic instrument, not only to identify technical vulnerabilities but also to quantify business risk, validate security investments, and build confidence with regulators, partners, and customers alike.
What is Web Application Penetration Testing?
Web application penetration testing is a structured security assessment in which ethical security professionals simulate real-world cyberattacks against a web application to identify, exploit, and evaluate vulnerabilities.
The objective is not only to uncover technical flaws, such as injection vulnerabilities, authentication weaknesses, or insecure configurations, but also to assess the potential business impact of those flaws, including data breaches, regulatory non-compliance, financial loss, and reputational damage.
The 2026 Web Application Threat Landscape
The landscape of web application threats now includes a combination of existing (and evolving) threats and emerging threats. We are already aware of the persistent yet evolving threats that include broken access control, injection attacks, insecure design, security misconfigurations, and more.
- AI-powered attacks: Exploits and automated phishing are widely accessible, shrinking response windows from weeks to hours. Patch cycles alone are no longer sufficient.
- API exposure: APIs now handle most enterprise traffic, yet many remain unmonitored, creating growing blind spots.
- Cloud misconfigurations: Microservices and containers multiply failure points. Small access gaps now lead to large breaches.
- Supply chain risk: A single compromised dependency can expose thousands of organizations.
- Regulatory pressure: Compliance alone is not enough. Leaders are expected to demonstrate active cyber governance and validation.
The threat landscape in 2026 is not just about new vulnerabilities; it is about compressed timelines, expanded attack surfaces, and rising accountability at the board level.
Why is penetration testing important?
On an important level, this confidence comes from being sure that your organization would have everything under control in case things go south. And penetration testing can help your organization do just that.
“If someone really tried to break into our systems, could they succeed?”
That is what penetration testing provides: an evidence-based answer.
Here is how it helps in doing so.
- It reveals the unknowns that tools cannot see
- It validates security investments
- It goes beyond compliance
- It drives continuous security improvement
- It builds a security-aware culture
Web application penetration testing Process
Penetration testing is not a single “hack attempt.” It is a structured methodology designed to replicate attacker behavior, but in a controlled way that provides business and technical insights. Here is how it unfolds:
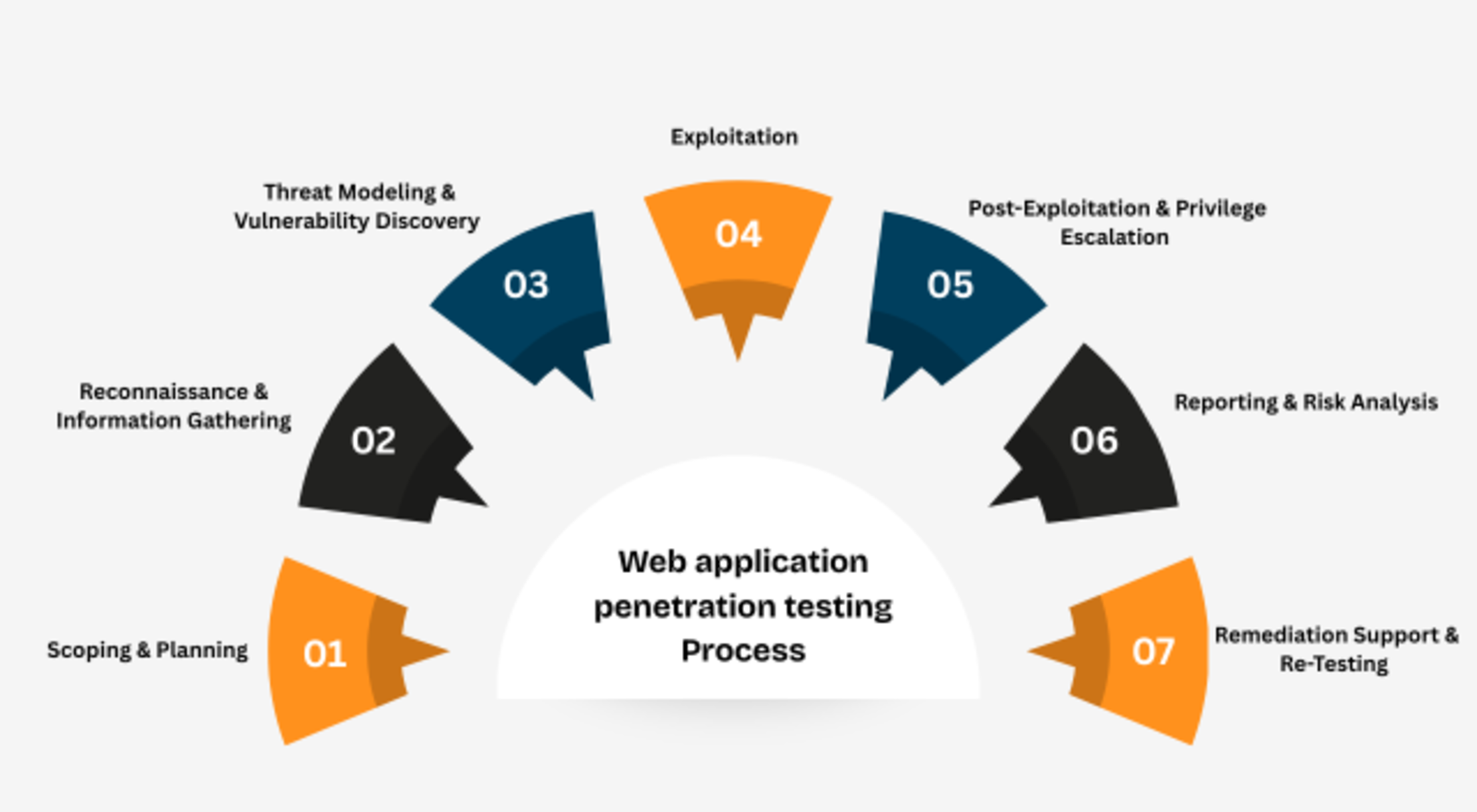
Step1: Scoping & Planning
Before testing begins, boundaries are set for which applications, APIs, or environments are in scope, and what business objectives the test should answer. It helps ensure testing aligns with strategic priorities (e.g., protecting customer data, securing payment flows) rather than chasing generic vulnerabilities.
Step 2: Reconnaissance and Information Gathering
Testers map the attack surface by collecting intelligence, domains, technologies, user flows, and integrations. This step provides visibility into what outsiders can see (including assets you may have forgotten), reducing “unknown unknowns.”
Step 3: Threat Modeling and Vulnerability Discovery
With the map in hand, testers identify attack paths. In this step, pen testers analyze how threats could exploit weaknesses, from misconfigurations to flawed logic, before attempting real attacks (not theoretical vulnerabilities).
Step 4: Exploitation
Here’s where theory becomes action. Testers safely attempt to exploit vulnerabilities, proving whether they are real risks or just noise. It may involve exploiting session management flaws, bypassing access controls, or exfiltrating test data via injection attacks. Payloads are carefully crafted to avoid production impact. It helps confirm which risks are real, so leadership does not waste time fixing false positives.
Step 5: Post-Exploitation and Privilege Escalation
Real attackers rarely stop at first access. Testers simulate lateral movement and privilege escalation to assess “blast radius.” The techniques may include privilege escalation, pivoting between internal apps, or accessing sensitive storage buckets and admin consoles. This step helps demonstrate the worst-case business scenario, e.g., could an attacker move from a single user account to financial databases?
Step 6: Reporting and Risk Analysis
Findings are consolidated into a report that balances technical depth with business clarity. Vulnerabilities are ranked by severity and likelihood, mapped to industry standards (CVSS, OWASP), and paired with remediation guidance. Reports usually include proof-of-concepts (PoCs), screenshots, and exploitation steps for dev teams. It provides a prioritized roadmap, not a raw data dump.
Step 7: Remediation Support and Re-Testing
The process ends with guided remediation and retesting to validate fixes. Without this, vulnerabilities remain theoretical. Developers often receive secure coding recommendations, configuration hardening guides, and re-scans to ensure closure.
Types of penetration testing for web applications
Not all penetration tests are alike. Different methods answer different business questions, like, “Can outsiders break in?” to “Are my developers coding securely?” Here are the major approaches:
Black Box Testing
Think of this as a “blind break-in.” Testers start with no insider knowledge, just like real attackers. It is the best way to simulate external threats and see how your defenses hold up against unknown outsiders.
White Box Testing (Clear/Glass Box)
The opposite extreme: testers get full access to architecture, source code, and credentials. It is less about surprise attacks and more about depth, uncovering subtle flaws in logic, design, or code quality.
Gray Box Testing
A balance between the two. Testers have partial knowledge (like user credentials or documentation), letting them dig deeper than a black box while still simulating realistic attacker scenarios. Ideal for time-efficient, business-focused testing.
Static Application Security Testing (SAST)
Here, the application never runs. Instead, testers (or automated tools) analyze source code line by line to spot insecure patterns. It is like proofreading before publishing, efficient for finding coding errors early in development.
Dynamic Application Security Testing (DAST)
DAST tests the app in action, simulating real-world attacks while the system is running. Think of it as a “mystery shopper,” interacting with the app as a user would, but probing for cracks. It is valuable for catching runtime vulnerabilities.
Interactive Application Security Testing (IAST)
A hybrid approach combines SAST’s deep code inspection with DAST’s live attack simulation. It runs within the app, providing developers with real-time feedback on where code execution and vulnerabilities meet. High ROI for modern DevSecOps pipelines.
API Penetration Testing
APIs are the “backbone” of modern apps and one of the fastest-growing attack targets. API pen testing validates authentication, authorization, and data handling, ensuring that sensitive information is not exposed through poorly protected endpoints.
Client-Side Penetration Testing
Security does not end at the server. Client-side testing examines JavaScript, browser interactions, and business logic flaws to prevent attacks like cross-site scripting (XSS) or manipulation of client code. It is crucial as apps increasingly shift logic to the front end.
Web application penetration testing tools
Some tools have become staples in every professional penetration tester’s arsenal. Here are the essentials and why they matter:
- Burp Suite intercepts and manipulates traffic to expose flaws in logins, transactions, and data submissions, showing executives real attacker risks.
- OWASP ZAP offers automated scanning, spidering, and CI/CD integration as a free alternative, embedding security in DevOps without licensing costs.
- Nikto quickly detects outdated software, weak headers, and config gaps, catching low-hanging fruit attackers target most.
- SQLMap automates SQL injection detection and data exfiltration, revealing how fast customer or financial data can be stolen.
- Postman crafts and tests API requests, securing the backbone of mobile apps, integrations, and digital services.
Conclusion: From Testing to Assurance
In 2026, web application penetration testing is no longer a technical exercise performed to satisfy compliance requirements. It is a strategic control that validates whether your defenses hold up under real-world pressure.
Threats are evolving faster. Attack surfaces are expanding. Regulatory expectations are tightening. In this environment, assumptions are liabilities.
Penetration testing provides evidence. Evidence shows that controls are effective, investments yield results, and risks are well understood.
Other Popular Articles
In the digital age, businesses must adopt an ad
GRC is the capability, or integrated collection










